
In today's fast-paced business landscape, staying ahead of the competition requires efficient and effective solutions. According to Microsoft’s Work Trend Index, nearly 70% of employee report that they don’t have sufficient time in the day to focus on “work”, with more time being spent Communicating than Creating.
Microsoft 365 Copilot is designed, with Microsoft’s cloud trust platform at its core, to allow for employees to both be more productive, reduce the time spent searching for information, performing mundane tasks, and other low-value activities.
Understanding the Limitations of Authentication Session Management with Conditional Access
New to conditional access is session control where you can define sign-in frequency and persistent browser session. This requires Azure AD P1.
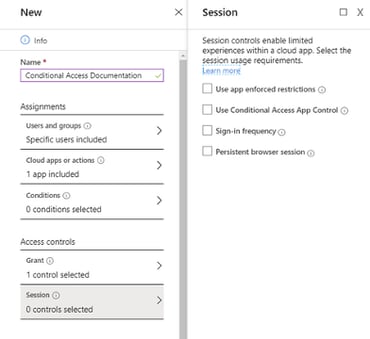
Microsoft defines sign-in frequency as the time period before a user is asked to sign in again when attempting to access a resource. This can be set to individual apps. This applies to both first and second factor in both client and browser. This means that if you require MFA in the same conditional access policy you are configuring session control with sign-in frequency, the user will be required to respond to MFA in addition to resupplying their password.
The persistent browser session option allows users to remain signed in after closing and reopening their browser window. Persistent browser session can only be set when all cloud apps are selected. This setting will overwrite the “Stay signed in?” setting in the company branding pane in Azure portal (if you have both policies configured) in addition to the “Remember MFA” setting in MFA cloud configuration settings.
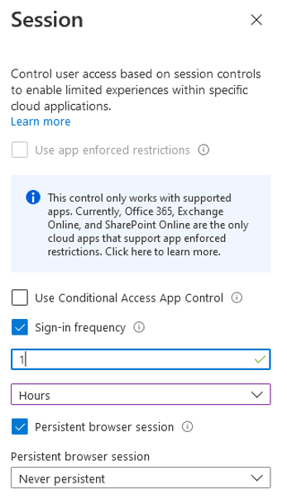
So let's look at a potential use case here. Let's say we have a user who manages a resource in Azure. In an effort to balance usability and security, we want to provide stricter session control when the user is accessing portal.azure.com. This is represented as the “Microsoft Azure Management” Cloud app in conditional access. So we make a set of conditional access policies – remember conditional access policies run asynchronously. Both policies are only targeted to this one user. We create one policy that restricts sign-in frequency to one hour – the lowest possible value – targeting the “Microsoft Azure Management” Cloud app. We create another policy targeting “All Cloud Apps” that sets the persistent browser session option to “Never Persistent.”
This works as expected on unmanaged devices. However, things do not work as you would expect when the device is Hybrid Azure AD joined with SSO configured. With these devices, a user will not be prompted again for a password when accessing portal.azure.com when using an SSO supported browser like Edge. Oddly enough, when we expand the sign-in frequency policy to include all apps, Outlook will get prompted for a password and MFA every hour, while accessing portal.azure.com from the Edge browser will only ever prompt for MFA. If MFA was done recently with another app on the same computer, you can open and close Edge and navigate to portal.azure.com with zero prompts!
The solution – for now – is to provide the user with a separate account with elevated permissions.
KiZAN is a Microsoft National Solutions Provider with numerous gold and silver Microsoft competencies, including gold security and gold enterprise mobility management. Our primary offices are located in Louisville, KY, and Cincinnati, OH, with additional sales offices located in Tennessee, Indiana, Michigan, Pennsylvania, Florida, North Carolina, South Carolina, and Georgia.





