
In today's fast-paced business landscape, staying ahead of the competition requires efficient and effective solutions. According to Microsoft’s Work Trend Index, nearly 70% of employee report that they don’t have sufficient time in the day to focus on “work”, with more time being spent Communicating than Creating.
Microsoft 365 Copilot is designed, with Microsoft’s cloud trust platform at its core, to allow for employees to both be more productive, reduce the time spent searching for information, performing mundane tasks, and other low-value activities.

Defend against Follina and DogWalk
On May 30th, 2022, Microsoft issued CVE-2022-30190
This was in reference to the Follina, the first zero-day. The guidance reads:
"A remote code execution vulnerability exists when MDST is called using the URL protocol from a calling application such as Word. An attacker who successfully exploits this vulnerability can run arbitrary code with the privileges of the calling application. The attacker can then install programs, view, change, or delete data, or create new accounts in the context allowed by the user’s rights."
It is believed that state-backed hackers are exploiting Follina via phishing campaigns aimed at US government agencies and European countries. Proofpoint has validated such suspicions in tweets last week.
Since Follina, a second zero-day, “Dogwalk”, has been discovered and there is no current CVE for this one. It also leverages the Microsoft Support Diagnostic Tool, to compromise the system.
Microsoft has not yet released a patch, so let’s get right into this and make sure we understand what our mitigation options entail based on guidance provided by Microsoft. Be sure to test and pilot any changes before deploying to production devices.
!!!UPDATE!!!
Start testing KB5014699 for Windows 10 and KB5014697 for Windows 11 today! This will resolve the MSDT.exe vulnerability. But do not stop there if you are running Microsoft Defender for Endpoint. You need Attack Surface Reduction Rules!
Update Microsoft Defender Antivirus
If you are not using MDAV as your primary AV solution, this fix is not for you.
This one is as simple as it gets. Deploy the latest MDAV signature updates as a quick way to protect systems while determining what the next step is for your organization. Make sure your version is 1.367.851.0 or higher. It’s as simple as that. Is it, though? Newly provisioned systems may be behind on updates, so be sure you have Microsoft Endpoint Manager (ConfigMgr or Intune) managing your Windows estate. Signature updates for MDAV should always be current, so hopefully, there is nothing for you to do here.
Deploy an Attack Surface Reduction Rule
The engine behind the ASR functionality is MDAV, not to be confused with Microsoft Defender for Endpoint (MDE), which is a cloud-based endpoint, detection, and response (EDR) solution. MDAV is available on all current Windows operating systems, however, if you are not using it as your primary AV solution, this fix is not for you.
If you have already deployed this ASR, you have already mitigated this vulnerability:
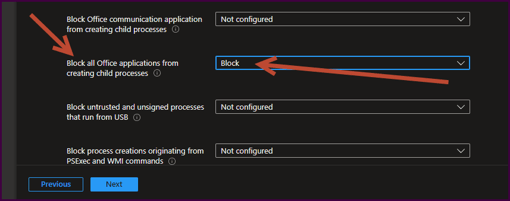
“Block all Office applications from creating child processes”
Requirements:
- Microsoft Defender Antivirus (MDAV) as the primary endpoint AV solution with real-time protection enabled
- Either Microsoft Endpoint Manager (MEM/Intune) OR Group Policy
Deploy in Microsoft Endpoint Manager
- Navigate to endpoint.microsoft.com (Microsoft Endpoint Manager admin center)
- Select Endpoint Security > Attack Surface Reduction > + Create Policy
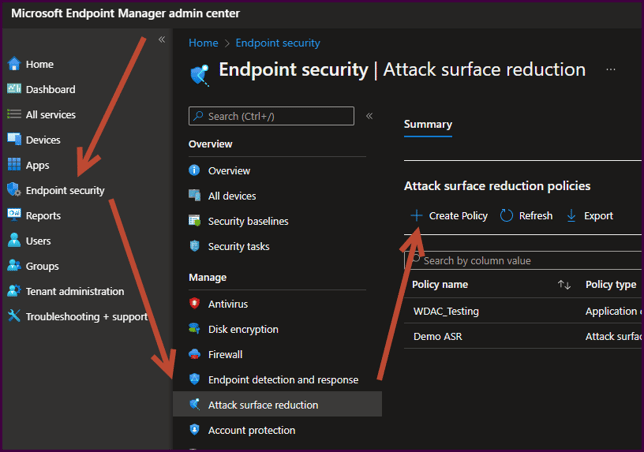
- On the “Create a Profile” blade
- Select “Windows 10 and later” from the “Platform” dropdown
- Select “Attack Surface Reduction Rules” from the “Profile” dropdown
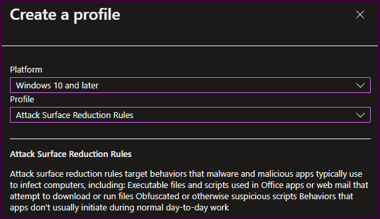
- Select “Create” at the bottom of the “Create a Profile” blade
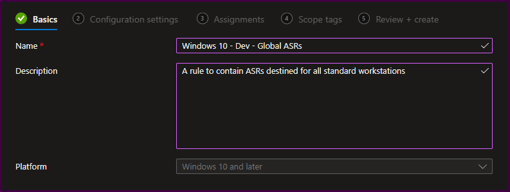
- Provide a name and description for the profile, then select “Next”
- Scroll down the list of rules and configure the “Block all Office applications from creating child processes” to block and select “Next”
- For “Assignments”, select a group of devices for testing to deploy the profile.
Once testing is complete, be sure to undergo an inclusive user pilot to collect feedback on any impact. An ASR policy profile can contain a list of exclusions if needed. ASRs can also be deployed to a user and Device Filters in MEM can also be leveraged for precise targeting of the ASR to endpoints.
Deploy in Group Policy
- Launch a Group Policy Management Console
- Create a test Group Policy for computer objects
- Launch the test policy in the Group Policy Editor
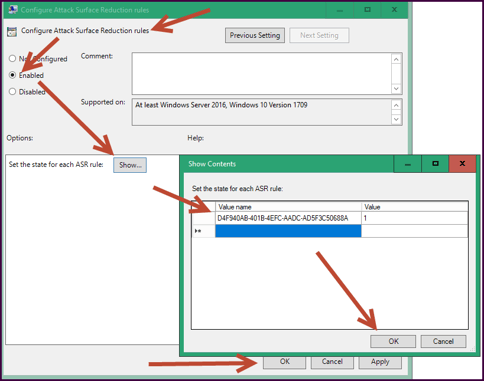
- Navigate to Computer Configuration > Administrative Templates > Windows Components > Microsoft Defender Antivirus > Microsoft Defender Exploit Guard > Attack Surface Reduction Rules
- Select the “Configure Attack Surface Reduction Rules” GPO Setting and toggle to “Enabled”
- Select “Show” and enter “D4F940AB-401B-4EFC-AADC-AD5F3C50688A” as the “Value Name” and “1”
- Select "Okay", then "Okay" again, then close the editor.
**Note: The ASR rule IDs are located here.
Disable the MSDT URL Protocol
If the two options above are not for you, this may be the only option. It is not preferred, but we use the tools we have!
Although effective (quick and dirty), this method will render the MSDT tool inoperable. If MSDT is required, you would recreate the removed registry key and values which seem to be the same across all Windows 10 devices. The guidance says to first backup the key, which is not feasible for hundreds and thousands of machines. Backing up a key for each OS version may be sufficient.
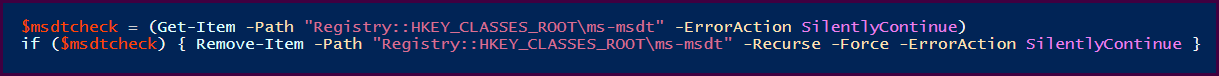
PowerShell to remove registry key if it exists
KiZAN is a Microsoft National Solutions Provider with numerous gold and silver Microsoft competencies, including gold data analytics. Our primary offices are located in Louisville, KY, and Cincinnati, OH, with additional sales offices located in Tennessee, Indiana, Michigan, Pennsylvania, Florida, North Carolina, South Carolina, Georgia and Texas.




