
In today's fast-paced business landscape, staying ahead of the competition requires efficient and effective solutions. According to Microsoft’s Work Trend Index, nearly 70% of employee report that they don’t have sufficient time in the day to focus on “work”, with more time being spent Communicating than Creating.
Microsoft 365 Copilot is designed, with Microsoft’s cloud trust platform at its core, to allow for employees to both be more productive, reduce the time spent searching for information, performing mundane tasks, and other low-value activities.

Two New Exchange Server Vulnerabilities Detected
Summary
Microsoft is investigating multiple zero-day vulnerabilities for Exchange Server 2013, 2016, and 2019. Attackers are exploiting these vulnerable Exchange Servers. There are no patches available as of yet, but Microsoft has released guidance on mitigating and identifying these threats. Although Exchange Online is not directly affected, most organizations still have Exchange Servers in their environment for full legacy management capabilities. Make sure none of these are internet facing. According to 3rd party stats, there are over 100,000 internet facing Exchange Servers. See the below guidance to protect your organization today.
Mitigations
Microsoft Exchange customers should review and apply the following URL Rewrite Instructions and block exposed Remote PowerShell ports.
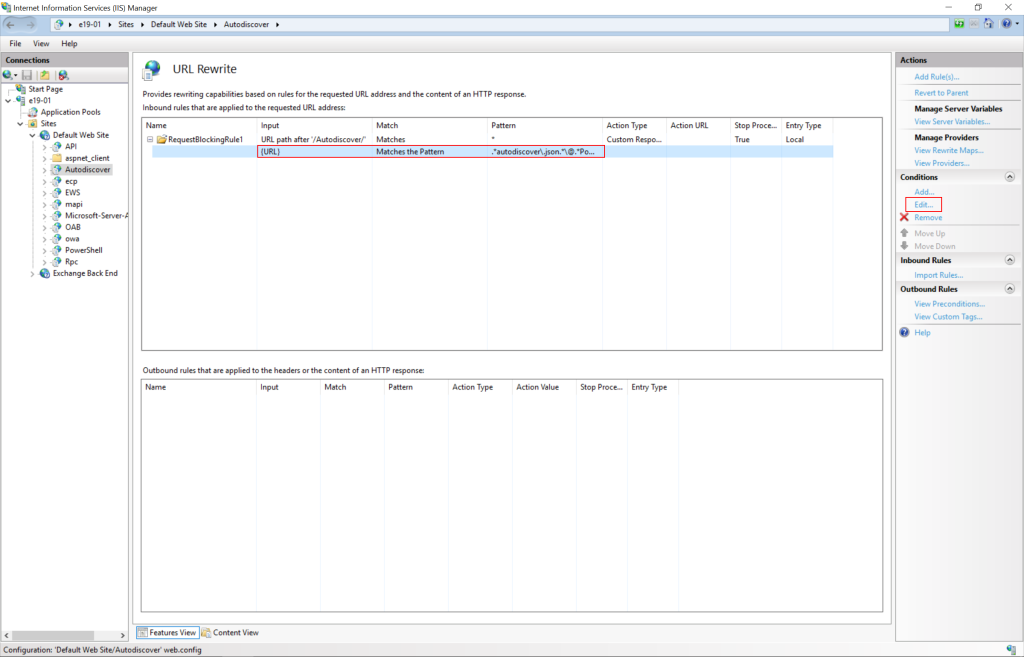
The current mitigation is to add a blocking rule in “IIS Manager -> Default Web Site -> Autodiscover -> URL Rewrite -> Actions” to block the known attack patterns.
Microsoft has confirmed that the following URL Rewrite Instructions, which are currently being discussed publicly, are successful in breaking current attack chains.
- Open the IIS Manager
- Expand the Default Web Site
- Select Autodiscover
- In the Feature View, click URL Rewrite
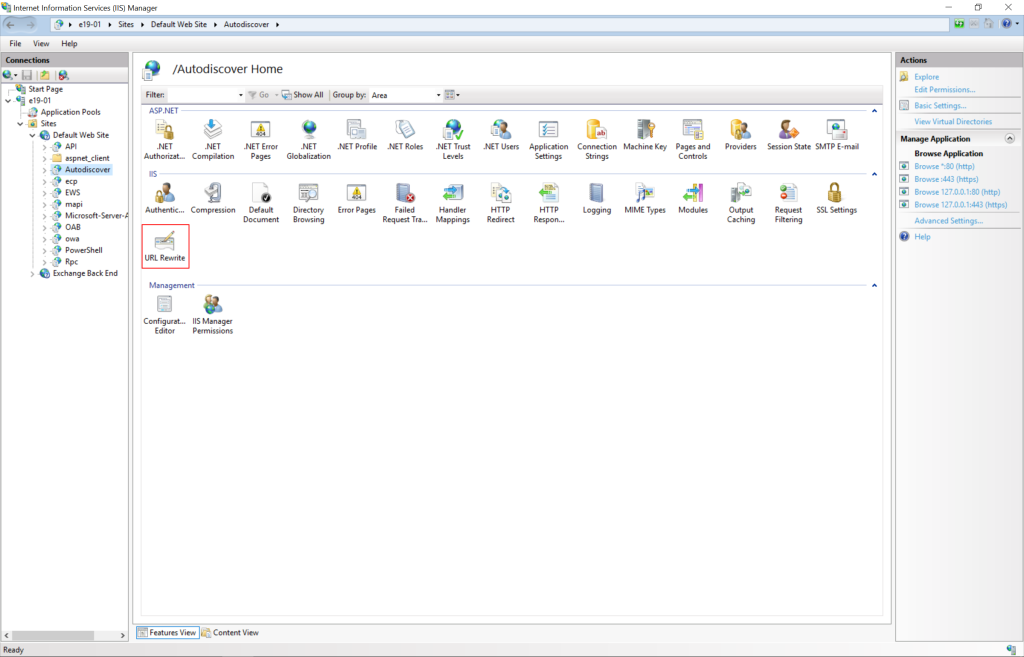
• In the Actions pane on the right-hand side, click Add Rules.
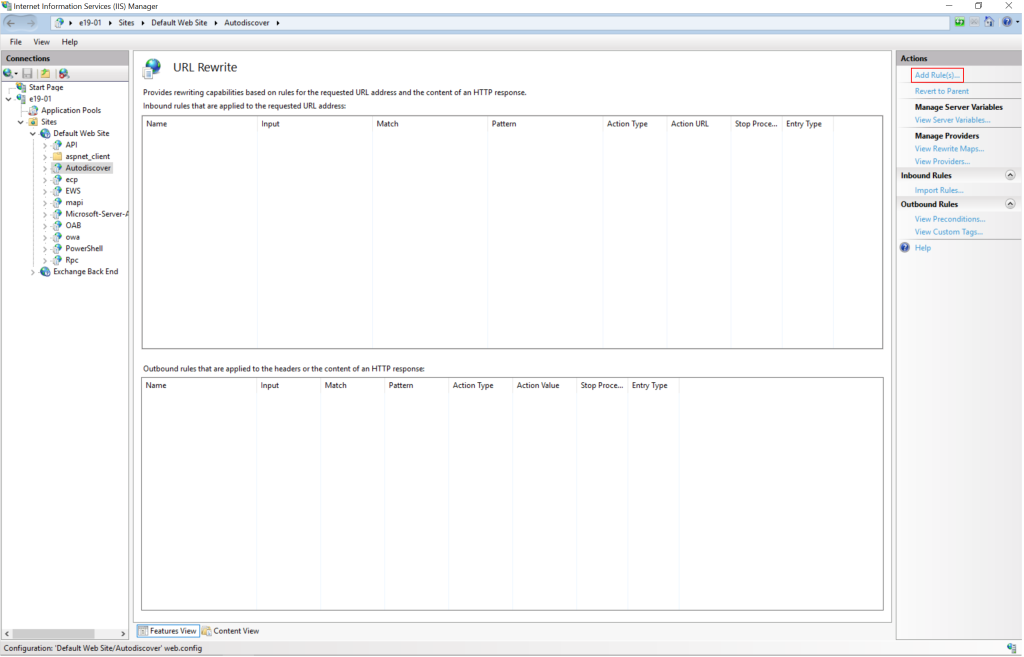
• Select Request Blocking and click OK.
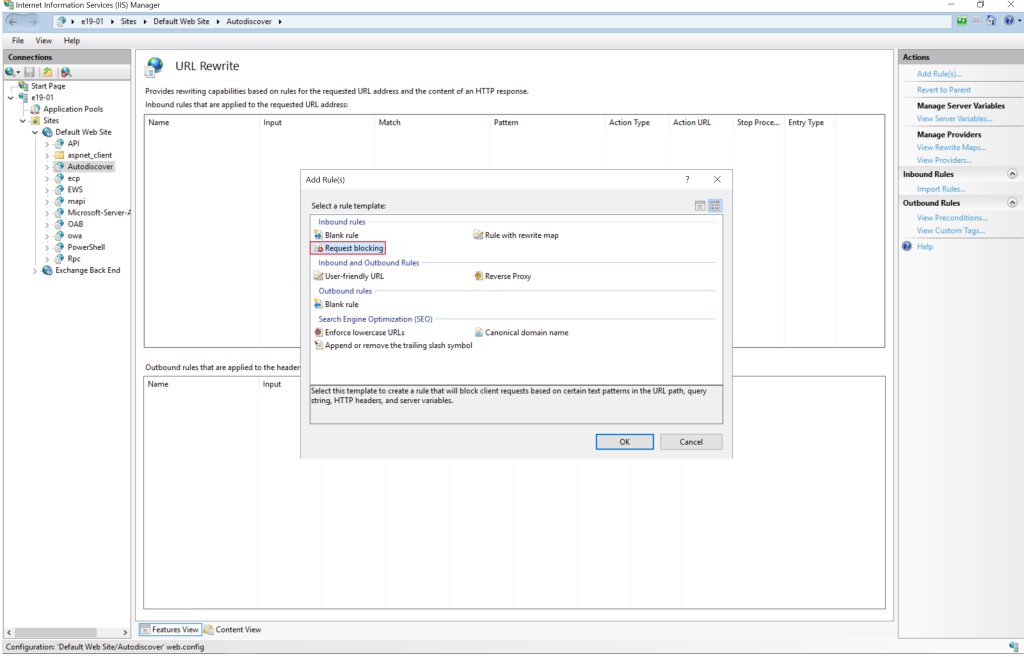
• Add String “.*autodiscover\.json.*\@.*Powershell.*” (excluding quotes) and click OK.
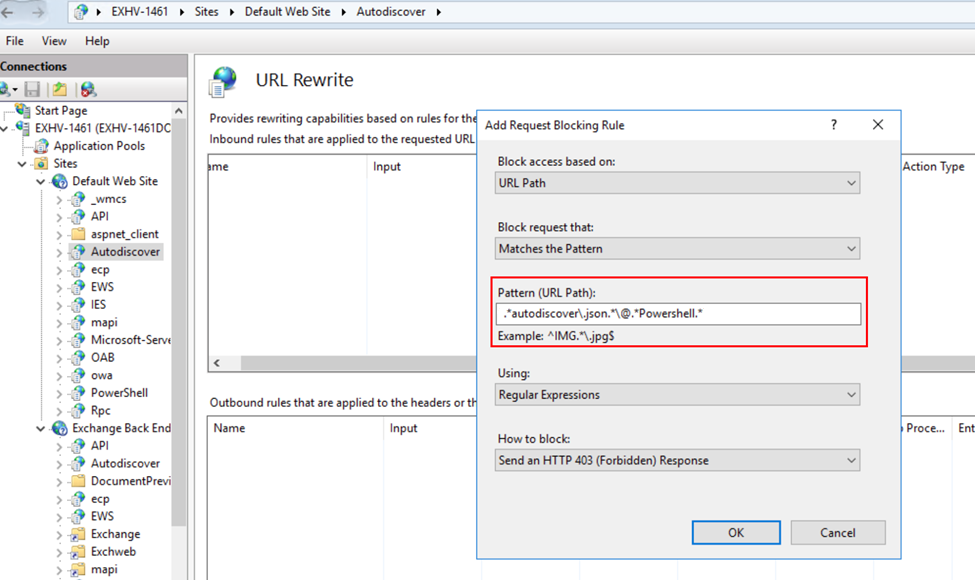
• Expand the rule and select the rule with the Pattern “.*autodiscover\.json.*\@.*Powershell.*” and click Edit under Conditions.
• Change the condition input from {URL} to {REQUEST_URI}
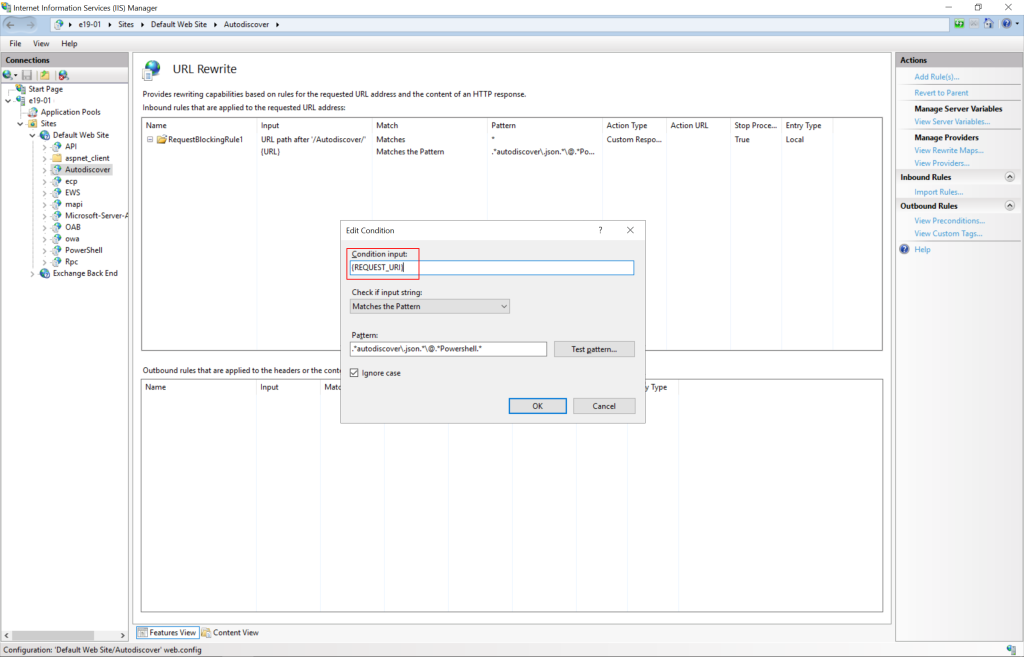
Impact: There is no known impact to Exchange functionality if the URL Rewrite module is installed as recommended.
Authenticated attackers who can access PowerShell Remoting on vulnerable Exchange systems will be able to trigger RCE using CVE-2022-41082. Blocking the ports used for Remote PowerShell can limit these attacks.
- HTTP: 5985
- HTTPS: 5986
Mitigations
While Microsoft does not currently have a specific detection query for this issue, based on what has been observed in the wild, the following techniques will help defenders. Microsoft's post on Web Shell Threat Hunting with Microsoft Sentinel also provides valid guidance for looking for web shells in general.
The Exchange SSRF Autodiscover ProxyShell detection, which was created in response to ProxyShell, can be used for queries as there are similarities in function with this threat. Also, there is a new Exchange Server Suspicious File Downloads query which specifically looks for suspicious downloads in IIS logs. In addition to those, there are a few more that could be helpful in looking for post-exploitation activity:
- Exchange OAB Virtual Directory Attribute Containing Potential Webshell
- Web Shell Activity
- Malicious web application requests linked with Microsoft Defender for Endpoint alerts
- exchange-iis-worker-dropping-webshell
- Web shell Detection
Microsoft Defender for Endpoint
Microsoft Defender for Endpoint detects post-exploitation activity. The following alerts can be related to this threat:
- Possible web shell installation
- Possible IIS web shell
- Suspicious Exchange Process Execution
- Possible exploitation of Exchange Server vulnerabilities
- Suspicious processes indicative of a web shell
- Possible IIS compromise
Defender for Endpoint customers with Microsoft Defender Antivirus enabled can also detect the web shell malware used in in-the-wild exploitation of this vulnerability with the following alerts:
- ‘Chopper’ malware was detected on an IIS Web server
- ‘Chopper’ high-severity malware was detected
Microsoft Defender Antivirus
Microsoft Defender Antivirus detects the post exploitation malware used in current in-the-wild exploitation of this vulnerability as the following:
- Backdoor:ASP/Webshell.Y (Backdoor:ASP/Webshell.Y threat description – Microsoft Security Intelligence)
- Backdoor:Win32/RewriteHttp.A (Backdoor:Win32/RewriteHttp.A threat description – Microsoft Security Intelligence)
Disclaimer: All information provided in this blog post comes directly from Microsoft Security and Response Center and is subject to change. Please see the following link for up-to-date information - https://msrc-blog.microsoft.com/2022/09/29/customer-guidance-for-reported-zero-day-vulnerabilities-in-microsoft-exchange-server/
Microsoft Sentinel Accelerator
See how Microsoft's SIEM, SOAR, and XDR can protect your organization.
KiZAN is a Microsoft National Solutions Provider with numerous gold and silver Microsoft competencies, including gold data analytics. Our primary offices are located in Louisville, KY, and Cincinnati, OH, with additional sales offices located in Tennessee, Indiana, Michigan, Pennsylvania, Florida, North Carolina, South Carolina, Georgia and Texas.




