
In today's fast-paced business landscape, staying ahead of the competition requires efficient and effective solutions. According to Microsoft’s Work Trend Index, nearly 70% of employee report that they don’t have sufficient time in the day to focus on “work”, with more time being spent Communicating than Creating.
Microsoft 365 Copilot is designed, with Microsoft’s cloud trust platform at its core, to allow for employees to both be more productive, reduce the time spent searching for information, performing mundane tasks, and other low-value activities.
Microsoft Defender External Attack Surface Management (EASM) is a comprehensive approach to managing and reducing the vulnerabilities and threats to a company's external attack surface. The external attack surface refers to the parts of a company's infrastructure and systems that are visible and accessible to external entities, such as hackers and cybercriminals.
EASM Discovery Process
EASM is a proactive approach to security that helps companies identify and prioritize potential vulnerabilities in their external attack surface and implement measures to mitigate those risks. It is a holistic approach that considers all aspects of a company's external attack surface, including web applications, networks, servers, and other internet-facing systems.
The following types of assets are included in the Defender EASM discovery process:
- Domains
- Pages
- IP Addresses
- Hosts
- IP Blocks
- Autonomous System Numbers (ASNs)
- SSL Certificates
- WHOIS Contacts
Assets Discovered by EASM
Below, you can see a list of assets discovered by EASM. These assets can be reviewed and approved/dismissed for external monitoring.
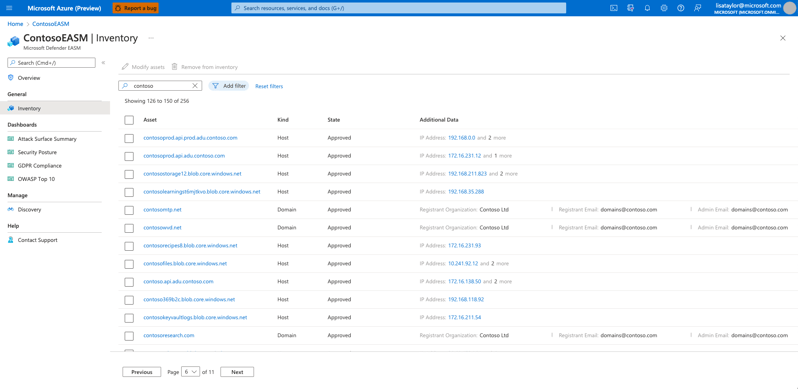
One of the key components of EASM is the use of threat intelligence to identify potential vulnerabilities and threats. This can include monitoring for known vulnerabilities, tracking the activities of known cybercriminals, and analyzing data from various sources to identify potential threats.
Once potential vulnerabilities and threats have been identified, EASM helps companies prioritize and address them based on their potential impact and likelihood of occurrence. This can involve implementing security measures such as firewall protection, intrusion detection systems, and vulnerability management systems.
One of the key benefits of EASM is that it helps companies anticipate and proactively address potential vulnerabilities and threats, rather than simply reacting to incidents after they occur. By continuously monitoring and managing the external attack surface, companies can significantly reduce their risk of being targeted by cybercriminals.
EASM Dashboards
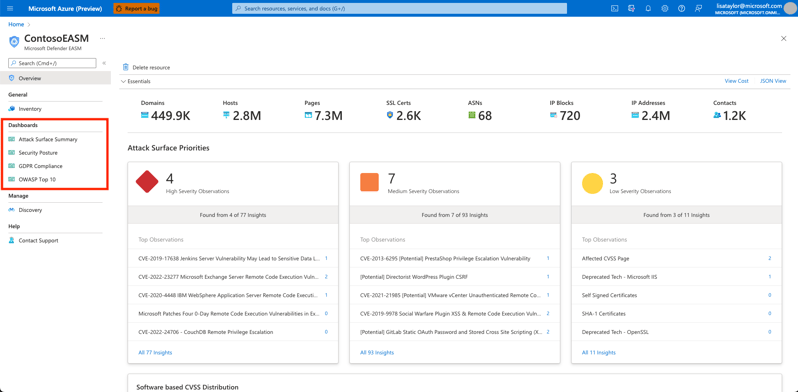
Microsoft Defender EASM offers four dashboards to help organizations prioritize vulnerabilities, risks, and compliance issues that pose the greatest threat to their attack surface and quickly mitigate key issues.
- The Attack Surface Summary dashboard provides a high-level overview of the organization's attack surface and potential vulnerabilities by severity, as well as insights into cloud hosting, sensitive services, SSL certificate and domain expiry, and IP reputation.
- The Security Posture dashboard helps organizations understand the maturity and complexity of their security program based on metadata from assets in the Confirmed Inventory, including technical and non-technical policies, processes, and controls that mitigate the risk of external threats.
- The GDPR Compliance dashboard identifies key areas of compliance risk based on the General Data Protection Regulation requirements for online infrastructure accessible to European nations, including website status, SSL certificate issues, exposed personal identifiable information, login protocols, and cookie compliance.
- The OWASP Top 10 dashboard surfaces assets that are vulnerable according to the Open Web Application Security Project's list of the most critical web application security risks, including broken access control, cryptographic failures, injections, insecure designs, and security misconfigurations.
In Conclusion
In conclusion, Microsoft Defender External Attack Surface Management is a comprehensive approach to managing and reducing the vulnerabilities and threats to a company's external attack surface. It involves the use of threat intelligence, technical measures, and processes and policies to anticipate and proactively address potential vulnerabilities and threats. By continuously monitoring and managing the external attack surface, companies can significantly reduce their risk of being targeted by cybercriminals and protect their sensitive data and systems.
Defender EASM is an affordable solution that offers a high value for the cost, and it now includes features to help you more easily track and manage your expenses. Be sure to approve or remove (dismiss) any assets you do not want to monitor. After 30 days, the cost of monitoring a resource at the time of this writing is $0.011 per day.
Microsoft Defender External Attack Surface Management - Pricing
KiZAN is a Microsoft National Solutions Provider with numerous gold and silver Microsoft competencies, including gold data analytics. Our primary offices are located in Louisville, KY, and Cincinnati, OH, with additional sales offices located in Tennessee, Indiana, Michigan, Pennsylvania, Florida, North Carolina, South Carolina, Georgia and Texas.




