In today's fast-paced business landscape, staying ahead of the competition requires efficient and effective solutions. According to Microsoft’s Work Trend Index, nearly 70% of employee report that they don’t have sufficient time in the day to focus on “work”, with more time being spent Communicating than Creating.
Microsoft 365 Copilot is designed, with Microsoft’s cloud trust platform at its core, to allow for employees to both be more productive, reduce the time spent searching for information, performing mundane tasks, and other low-value activities.
If you have collided with M365 licensing, you have no doubt heard the acronym “MPIP." But what is Microsoft Purview Information Protection (now known as Microsoft Purview Information Protection)? How can it help protect an organization's information? Is there a specific MPIP console that you somehow missed?
Well good news, there is no MPIP console! MPIP is a collection of tools comprised mainly of Azure Information Protection (AIP), Purview Data Loss Prevention (DLP), Defender for Cloud Apps (MDCA, formerly MCAS), and Windows Information Protection (WIP). There are several other tools like Azure Purview (preview) and Office Mail Encryption that could arguably be considered MPIP, but we will focus on the 4 pillars outlined above. Be sure to stick around till the end because we are saving the best for last!
Windows Information Protection
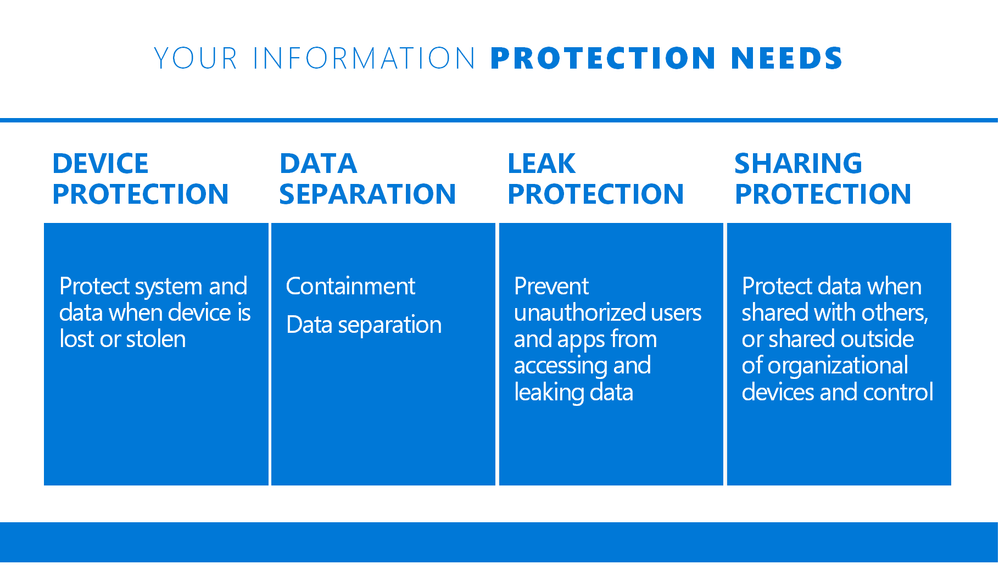
Windows Information Protection – In my opinion, the black sheep of MPIP is WIP. This is an E3/A3 benefit that is also known as “App Protection” in the Intune management console. The main goal of WIP is to prevent accidental data leakage by defining enterprise boundaries for data.
It allows for the management of apps independently or as a supplement to managed devices providing more granular capabilities. One main benefit of WIP, like mobile application management (MAM), is the ability to remove corporate data from devices without the need to completely wipe the device.
The most notable use for WIP is BYOD scenarios, allowing organizations to forgo full device management. I find many organizations do not know about WIP or are not managing Windows devices with Intune yet. Those days are numbered!
Figure A: Introducing Windows Information Protection - Microsoft Tech Community
Azure Information Protection
Azure Information Protection – Sensitivity labels provide data classification and optional protection of files and emails in SharePoint, OneDrive, Exchange, and on-premises repositories. A label taxonomy is defined to represent the various levels of classification required for an organization. Sensitivity labels travel with the document or email to which they are applied, protecting them wherever they are.
With E3/A3 licensing alone, files and emails must be manually labeled via the Unified Labeling Client. This means that creation or interaction with the file is required, and labeling is at the mercy of end-users. What could go wrong?
E5/A5 licensing gives you automatic labeling based on sensitive information types. This can be while the user interacts with a file or email, but files can also be labeled at rest via Microsoft Defender for Cloud Apps. Although I call out MDCA separately below, it’s important to understand it will be part of your labeling solution for SharePoint, OneDrive, as well as 3rd party apps like Box, Dropbox, and Google Drive.
You can also apply labels to SharePoint sites and Teams to provide additional protection capabilities. If applied to a SharePoint site, download restrictions can be put in place for untrusted devices, and/or sharing capabilities can be restricted beyond the organization’s global configuration.
If a label is applied to a Team, it can dictate if the team is public or private in addition to preventing external identities from being added to the Team.
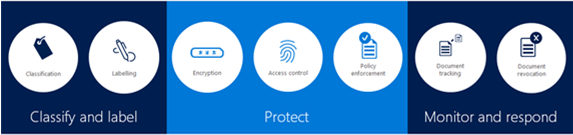
Figure B: Using Azure Information Protection to classify and label corporate data (microsoft.com)
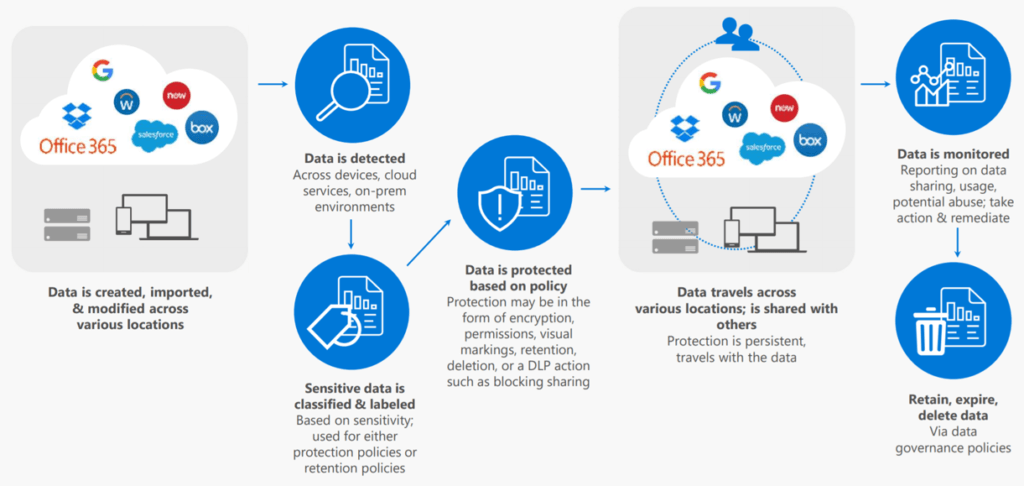
Figure C: Retention & Sensitivity Labels – Breaking down labeling in Microsoft 365
Purview Data Loss Prevention
Purview Data Loss Prevention – In contrast to AIP which applies a sensitivity label that travels with the document/email, DLP is “in-line” protection that can prevent, notify, and/or alert on sharing practices that conflict with the organizational policy.
As an example, let’s presume our org policy states no content should be shared externally if it contains 5 or more credit card numbers. A DLP policy could be configured to prevent the sharing of said content and notifications can be configured for the user sharing the content, content owners, and/or administrators via email or alert. Overrides could also be enabled to allow users to circumvent protections with justification that is stored in the audit log for tracking purposes.
While SharePoint, OneDrive, and Exchange are top of mind and available for E3/A3 licensing SKUs, E5/A5 licensing enables additional capabilities, one of which is Teams chat and channel messages.
Yes, content in teams will be covered via SharePoint and Exchange DLP policies, but messaging protection will require a licensing “level-up”. If the M365 E5/A5 is not in your wheelhouse, you will need the M365 E5/A5 compliance add-on to protect chat and channel messages.
Like Teams chat and channel messages, these capabilities require E5/A5 licensing as well:
- DLP for Endpoint – When sensitive data is detected, you can:
- Control uploads to cloud services
- Prevent unauthorized browsers
- Prevent copy to another app
- Prevent copy to USB removable media
- Prevent copy to network share
- Prevent printing
- Prevent copying to a remote session
- Prevent copying to a Bluetooth device
- Defender for Cloud Apps – Control sensitive information in 3rd party apps
- On-premises Repositories – Detect on-prem sensitive information and act
- PowerBI (Preview) – Enforce DLP policies in PowerBi, even when data is exported
A true “better together” technology combo, DLP can harvest all that technical equity put into AIP labels by including them as conditions for DLP policy matching!
Microsoft Defender for Cloud Apps
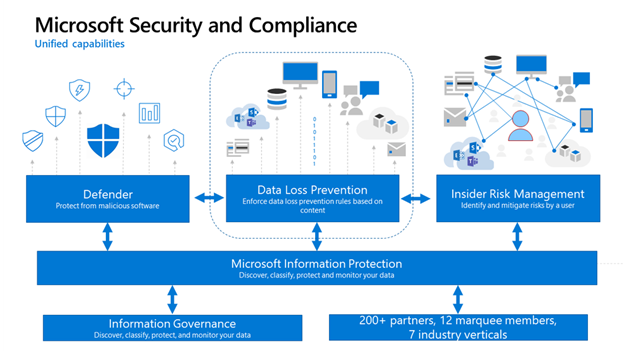
Microsoft Defender for Cloud Apps – While AIP is great at protecting information during file interaction and DLP is great for protecting share activities, MDCA is great for labeling data at rest and preventing data egress when combined with Conditional Access App Control.
Better known by its previous acronym (MCAS), MDCA is Microsoft’s implementation of a cloud app security broker, or CASB. Although its full capabilities extend well beyond MPIP, MDCA provides rich integration with Microsoft services in addition to MPIP and data governance controls for 3rd party storage providers (e.g. Dropbox, Google Drive).
With so many capabilities, it may not surprise you to learn that MDCA is an E5/A5 licensed product.
With MDCA, you can enact the following controls for SharePoint and OneDrive. 3rd party apps have fewer options, but you can label and perform some other removal options seen here:
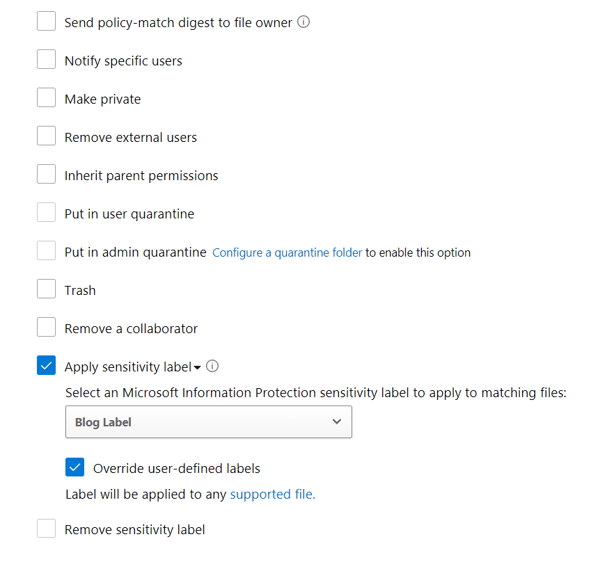
If you want full AIP and DLP capabilities, MDCA is a must-have. You can’t complete protection without it. And while you are deploying, you may as well take advantage of all the other features that come with MDCA. Check out these top 20 use cases for MDCA: Top 20 Use Cases for CASBs (microsoft.com)
There you have it! MPIP is a goal that requires multiple technologies to achieve. Having the right “stack” of products is great, but the magic is within the integration of those products. Combining MPIP with Microsoft Defender products such as Defender or Endpoint can provide next-level insight and control of organizational data.
KiZAN is a Microsoft National Solutions Provider with numerous gold and silver Microsoft competencies, including gold data analytics. Our primary offices are located in Louisville, KY, and Cincinnati, OH, with additional sales offices located in Tennessee, Indiana, Michigan, Pennsylvania, Florida, North Carolina, South Carolina, Georgia and Texas.